Protecting Consumer Privacy and Maximizing the Benefits of Big Energy Data
Update! Check out a recent report from WGN on the smart meter rollout in the Chicago area. The report looks at how residential customers can benefit and who gets access to the smart meter data. Here’s our coverage: Who Can Access Your Smart Meter Information?
This post is written by Marcella Bondie Keenan, policy fellow at Elevate Energy.
In February 2015, Elevate Energy and ComEd were invited to present at the Minnesota Public Utility Commission’s Energy Privacy Customer Data Series about ComEd’s best-in-class Energy Use Data System. This post is a summary of the discussion and our suggested path forward.
 Protecting Data Privacy
Protecting Data Privacy
In the U.S., smart meters have been installed in 43 percent of homes. This Advanced Metering Infrastructure (AMI) promises to unlock “big data” by providing nearly real-time information about energy use. The challenge is to capture the robust benefits of this AMI data while protecting consumer privacy rights.
Currently, there is no national standard to regulate how utilities and third parties, such as energy efficiency program providers, share and use consumer energy use data. State utility regulators typically rely on some combination of restrictions that define what data can be released, how the data can be used, and who may receive customer energy data.
What Data Can Be Released
Anonymity restrictions limit what data can be shared by a utility. Anonymization strips data of information that could identify an individual consumer. The anonymized data is then summed. The summed data set could be large or small, including all residential customers in a community, or all tenants in a building. How the data is anonymized may impact how it can be used to design energy efficiency programs or to target programs to the customers who would benefit the most.
How the Data Can Be Used
Data use restrictions limit how the data can be used. For example, state utility regulators may allow data to be used for energy efficiency program evaluation, but not for marketing purposes. This could limit the ability of program providers to perform targeted outreach to customers with higher than average energy use.
Who Can Receive Customer Energy Data
Recipient restrictions limit who can access data. Generally, consumers are allowed to access their own energy data. They may also choose to download and share it with a third party. For example, Green Button is a technical standard that facilitates the development of data sharing software. However, the data sharing process places the burden on the consumer to access and share data. In some cases, regulators may allow third parties to perform the data download process for the consumer if the consumer has authorized them to do so.
Striking the Balance: A Real-World Example in Illinois
ComEd , the utility that delivers electricity to nearly 4 million customers in northern Illinois, has developed an Energy Use Data System (EUDS) that strikes a productive balance between using data to move energy efficiency forward and protecting consumer privacy.
, the utility that delivers electricity to nearly 4 million customers in northern Illinois, has developed an Energy Use Data System (EUDS) that strikes a productive balance between using data to move energy efficiency forward and protecting consumer privacy.
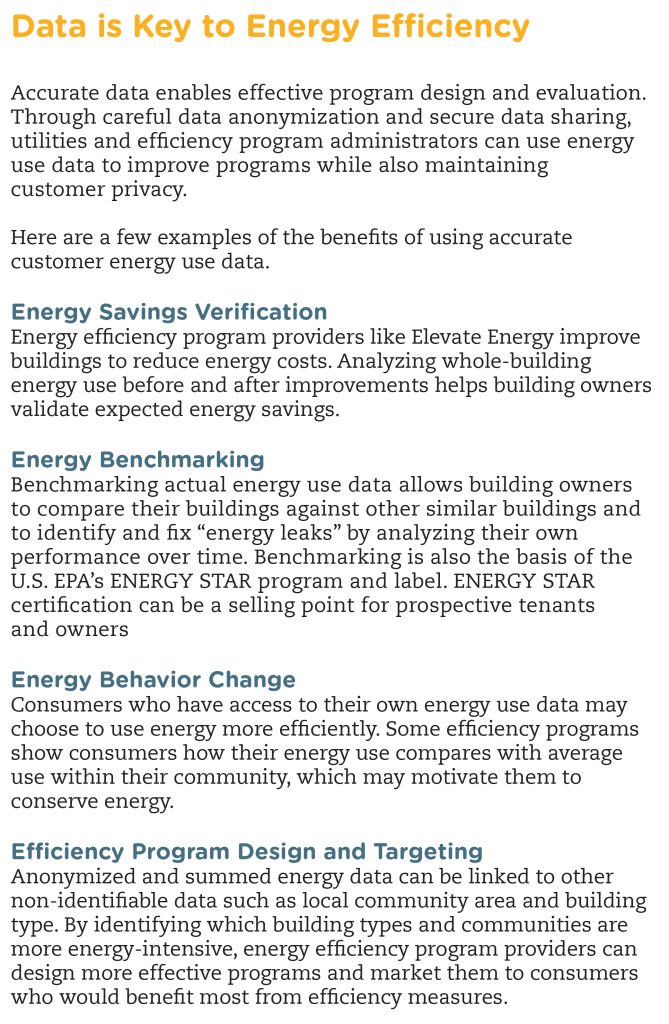
The EUDS system allows eligible building owners to securely and easily access their own energy data. Owners may access EUDS by enrolling a building in ComEd’s energy benchmarking program, or by installing efficiency measures through Elevate Energy’s buildings program. Owners can enroll a single building or their entire portfolio, receiving anonymized, summed electricity usage for each building.
EUDS enables owners to automatically export monthly data to the U.S. Environmental Protection Agency’s ENERGY STAR Portfolio Manager using secure data transmission. Benchmarking helps owners compare their building against other similar buildings and to identify and fix “energy leaks” by analyzing their own performance over time.
ComEd’s EUDS system protects consumer privacy in several ways. First, it maintains the tenant privacy, because the building owner never sees an individual customer’s usage information. To be eligible to receive data through EUDS, the building must have at least four utility customers, and no one customer can represent more than 80 percent of the total building energy use. Energy use data is only provided as summed information (one kWh usage number for the entire building, for each month).
Second, ComEd also restricts who can receive data. Only verified building owners can enroll in and access the EUDS system. ComEd only shares usage data and login information with the building owner and will not grant access to third parties. However, individual building owners may choose to share their EUDS login or building data with a third party, including energy efficiency program providers.
 The Path Forward
The Path Forward
Data privacy is important. Utilities like ComEd are leaders in developing data systems that support energy efficiency and benchmarking programs while also securely protect customer data. Regulators, energy efficiency advocates, and industry stakeholders also have a role to play in balancing effective energy use data and consumer privacy.
Stakeholders can help increase awareness of useful energy data. For example, energy efficiency programs may benefit from both individual energy use data and building-level or geographic data. This merged dataset would provide more granular detail on which types of buildings and which communities are achieving the greatest energy efficiency gains. In this case, to ensure consumer privacy, data could be fully anonymized after the datasets are merged and before they are shared with any third party.
Developing industry-wide technical standards and regulatory definitions for energy data access will also help. This will enable utilities and third-party energy efficiency providers to foster a trusted relationship with regulators and customers. However, it is important to recognize that each region has unique needs that must be considered in order to achieve maximum benefits. For example, building density, which varies widely by community, could impact the protocol for anonymizing data.
Additional Resources
- Alissa Burger, Institute for Market Transformation. November 17, 2014. “HUD Supports Utility Data Access.” http://www.imt.org/news/the-current/hud-supports-utility-data-access
- City of Chicago. 2014 Building Energy Benchmarking Report. http://www.cityofchicago.org/content/dam/city/progs/env/EnergyBenchmark/2014_Benchmarking_Report_Final.pdf
- The Edison Foundation. Institute for Electric Innovation. September 2014. Utility-Scale Smart Meter Deployments: Building Block of the Evolving Power Grid. http://www.edisonfoundation.net/iei/Documents/IEI_SmartMeterUpdate_0914.pdf
- Elevate Energy. 2014. “Aggregated Data Access: The 15/15 Rule in Illinois and Beyond.” https://www.elevatenp.org/wp-content/uploads/1515-Rule-Factsheet-FINAL.pdf
- Green Button Connect. http://www.greenbuttonconnect.com/
- Lawrence Kotewa, Elevate Energy. February 13, 2015. “Aggregate Energy Usage Data and Energy Efficiency in Multifamily Affordable Housing.” Presentation to Minnesota Public Utilities Commission. http://mn.gov/puc/documents/pdf_files/privacy_workshop_elevate_energy_usage_data_aggregation_2-13-2015.pdf
- Anne McKibbin, Elevate Energy. August 2014. “Unleashing the Power of Big Data on Efficiency? Not so Fast.” ACEEE Summer Study. https://www.elevatenp.org/wp-content/uploads/Unleashing_Power_Big_Data_Efficiency_ACEEE_2014.pdf
- Energy Information Administration. December 11, 2011. Smart Grid Legislative and Regulatory Policies and Case Studies. http://www.eia.gov/analysis/studies/electricity/



